Azure Active Directory : 7 Powerful Insights You Must Know
Welcome to the ultimate guide on Azure Active Directory (AAD), your go-to resource for mastering identity and access management in the cloud. Whether you’re an IT pro or just starting out, this deep dive will simplify AAD’s complex features with real-world insights and expert tips.
What Is Azure Active Directory (AAD)? A Foundational Overview

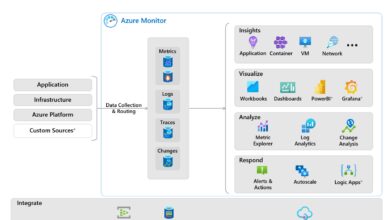
Azure Active Directory (AAD) is Microsoft’s cloud-based identity and access management service, designed to help organizations securely manage user identities and control access to applications and resources. Unlike the traditional on-premises Active Directory, AAD is built for the modern, cloud-first world, supporting hybrid environments, multi-factor authentication, and seamless integration with thousands of SaaS applications.
How AAD Differs from On-Premises Active Directory
While both systems manage identities, their architectures and use cases differ significantly. On-premises Active Directory relies on domain controllers and LDAP protocols within a local network, whereas AAD operates in the cloud using REST APIs and OAuth protocols. This shift enables global scalability and faster deployment.
- On-prem AD uses NTLM/Kerberos for authentication; AAD uses modern protocols like OAuth 2.0, OpenID Connect, and SAML.
- AAD supports device registration instead of domain joining, enabling easier management of mobile and remote devices.
- Global reach: AAD automatically replicates data across Microsoft’s global data centers for high availability.
“Azure AD is not just ‘Active Directory in the cloud’—it’s a reimagined identity platform for modern workforces.” — Microsoft Tech Community
Core Components of Azure Active Directory
AAD is composed of several key components that work together to deliver secure, scalable identity management:
- Users and Groups: Central entities for assigning permissions and managing access.
- Applications: Represent software that users can sign into, whether cloud-based (like Salesforce) or custom-developed.
- Devices: Registered or joined devices that are recognized by AAD for conditional access policies.
- Roles and Administrators: Predefined and custom roles that allow granular control over who can manage what in AAD.
These components form the backbone of identity governance and are essential for implementing Zero Trust security models.
Azure Active Directory (AAD) Authentication Methods Explained
Authentication is at the heart of AAD’s functionality. It ensures that only verified users and devices gain access to corporate resources. AAD supports a wide range of authentication mechanisms, from simple passwords to advanced biometric verification.
Password-Based vs. Passwordless Authentication
Traditionally, users authenticate with a username and password. However, AAD now promotes passwordless authentication to reduce phishing risks and improve user experience.
- Password-based: Still supported but discouraged due to security vulnerabilities.
- Passwordless options: Include Windows Hello, FIDO2 security keys, Microsoft Authenticator app, and SMS/email one-time codes.
According to Microsoft, organizations using passwordless methods see up to a 67% reduction in helpdesk calls related to password resets.
Multi-Factor Authentication (MFA) in AAD
MFA adds an extra layer of security by requiring users to verify their identity through at least two methods. In AAD, MFA can be enforced via:
- Mobile app notifications (push)
- Time-based one-time passwords (TOTP)
- Voice calls or SMS (less secure but widely used)
AAD Conditional Access policies can dynamically require MFA based on risk level, location, or device compliance. For example, a login attempt from an unfamiliar country might trigger MFA even if the password is correct.
Key Features of Azure Active Directory (AAD) You Should Know
Azure Active Directory (AAD) offers a robust suite of features that empower organizations to manage identities securely and efficiently. From single sign-on to identity protection, these tools are critical for modern IT environments.
Single Sign-On (SSO) Across Cloud and On-Premises Apps
SSO allows users to access multiple applications with one login, improving productivity and reducing password fatigue. AAD supports SSO for over 2,600 pre-integrated SaaS apps, including Office 365, Salesforce, and Dropbox.
- Users sign in once and gain access to all authorized apps without re-entering credentials.
- SSO works via SAML, OAuth, or password vaulting for legacy systems.
- Hybrid SSO is possible using Azure AD Application Proxy for on-prem apps.
Learn more about SSO setup in Microsoft’s official documentation: Azure AD SSO Guide.
Conditional Access and Risk-Based Policies
Conditional Access is one of AAD’s most powerful security features. It enables administrators to set rules that control access based on specific conditions.
- Conditions include user location, device compliance, sign-in risk, and application sensitivity.
- Example policy: Block access from outside the corporate network unless the device is compliant and MFA is completed.
- Integrated with Identity Protection to respond to risky sign-ins automatically.
“Conditional Access turns static policies into dynamic, context-aware security controls.” — Microsoft Security Blog
Azure Active Directory (AAD) Licensing Tiers: Free vs. Premium
AAD comes in four main editions: Free, Office 365 apps, Premium P1, and Premium P2. Each tier unlocks additional features, making it crucial to choose the right one for your organization’s needs.
Feature Comparison Across AAD Tiers
Understanding the differences between tiers helps organizations optimize cost and security.
- Free: Basic identity management, SSO, MFA for self-service, 99.9% SLA.
- Office 365 apps: Includes Free features plus self-service password reset for cloud users.
- Premium P1: Adds Conditional Access, group-based licensing, hybrid identity, and Azure AD Join.
- Premium P2: Includes Identity Protection, Privileged Identity Management (PIM), and advanced risk detection.
For detailed comparisons, visit: Azure AD Editions Overview.
When to Upgrade to AAD Premium P1 or P2
Organizations should consider upgrading when they need:
- Advanced security controls like Conditional Access or Identity Protection.
- Hybrid identity management with seamless synchronization from on-prem AD.
- Just-in-Time (JIT) access for administrators via Privileged Identity Management.
- Compliance reporting and audit trails for regulatory standards like GDPR or HIPAA.
Many enterprises find that the ROI from reduced breach risks and improved operational efficiency justifies the premium cost.
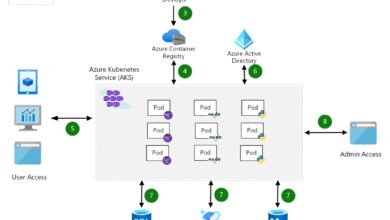
Hybrid Identity: Integrating On-Prem AD with Azure Active Directory (AAD)
Most organizations operate in a hybrid environment, maintaining on-premises infrastructure while adopting cloud services. AAD supports this model through seamless integration with on-prem Active Directory via Azure AD Connect.
What Is Azure AD Connect and How Does It Work?
Azure AD Connect is the primary tool for synchronizing user identities from on-prem AD to AAD. It ensures that users have a consistent identity across both environments.
- Performs password hash synchronization, pass-through authentication, or federation (AD FS).
- Supports group, contact, and device synchronization.
- Can be configured for staged rollout and filtering (e.g., sync only specific OUs).
Best practices recommend using Pass-through Authentication with Seamless SSO for better performance and reduced infrastructure overhead compared to AD FS.
Best Practices for Managing Hybrid Identities
To ensure a smooth hybrid identity experience:
- Regularly monitor sync health using the Azure AD Connect Health service.
- Implement proper naming and attribute flow rules to avoid conflicts.
- Use UPN matching to align on-prem and cloud usernames.
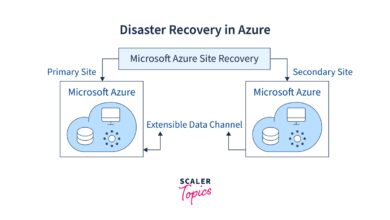
- Plan for disaster recovery by configuring redundancy and backup servers.
Microsoft provides a comprehensive guide at: Hybrid Identity Design Guide.
Security and Compliance in Azure Active Directory (AAD)
Security is a top priority in any identity system, and AAD offers robust tools to detect, prevent, and respond to threats. With rising cyberattacks targeting credentials, AAD’s security features are more critical than ever.
Identity Protection and Risk Detection
Azure AD Identity Protection uses machine learning to detect suspicious sign-in behaviors and compromised accounts.
- Identifies risks such as sign-ins from anonymous IPs, unfamiliar locations, or malware-infected devices.
- Assigns risk levels (low, medium, high) to users and sign-ins.
- Automatically blocks or requires MFA for high-risk events via Conditional Access policies.
This proactive approach helps stop breaches before they escalate.
Privileged Identity Management (PIM) for Just-in-Time Access
PIM is a premium feature that allows organizations to implement least-privilege access for administrators.
- Privileged roles (e.g., Global Admin) are not permanently assigned but activated on-demand.
- Admins must request access, provide justification, and complete MFA.
- Access duration is time-limited (e.g., 4 hours), reducing the attack surface.
“PIM reduces the risk of privileged account misuse by 80%.” — Microsoft Security Research
Managing Users, Groups, and Roles in Azure Active Directory (AAD)
Effective user and role management is essential for maintaining security and operational efficiency in AAD. Proper configuration ensures that users have the right access at the right time—no more, no less.
User Lifecycle Management: From Onboarding to Offboarding
AAD supports automated user provisioning and deprovisioning through integration with HR systems and SCIM (System for Cross-domain Identity Management).
- When a new employee is added in Workday or SAP, AAD can automatically create their account and assign licenses.
- Upon termination, accounts are disabled or deleted, and access is revoked across all connected apps.
- Reduces the risk of orphaned accounts and insider threats.
For setup instructions, refer to: Automated User Provisioning in AAD.
Role-Based Access Control (RBAC) in AAD
RBAC allows administrators to assign permissions based on job functions rather than individual users.
- Predefined roles include Global Administrator, User Administrator, Helpdesk Administrator, and more.
- Custom roles can be created for specific needs (e.g., a ‘Billing Reader’ role).
- Role assignments can be scoped to specific applications or groups.
Using RBAC minimizes the risk of privilege creep and simplifies audits.
Common Challenges and Best Practices for Azure Active Directory (AAD) Deployment
While AAD offers powerful capabilities, its deployment can present challenges, especially in complex environments. Understanding common pitfalls and best practices ensures a smoother implementation.
Common AAD Deployment Pitfalls
Organizations often encounter issues such as:
- Incorrect attribute mapping during synchronization, leading to login failures.
- Over-permissioned roles, increasing the risk of privilege abuse.
- Poor Conditional Access policy design, causing user lockouts or security gaps.
- Lack of monitoring, making it hard to detect sync errors or suspicious activity.
Thorough planning and testing in a pilot environment can prevent most of these issues.
Best Practices for AAD Success
To maximize the value of AAD:
- Start with a clear identity strategy and governance model.
- Enable MFA for all users, especially administrators.
- Use Conditional Access to enforce device compliance and location-based rules.
- Regularly review sign-in logs and risky user reports.
- Train IT staff and end-users on new authentication methods and security policies.
Microsoft’s AAD documentation is a valuable resource: Azure Active Directory Documentation.
What is Azure Active Directory (AAD)?
Azure Active Directory (AAD) is Microsoft’s cloud-based identity and access management service that enables secure user authentication and resource access across cloud and on-premises applications.
How does AAD differ from traditional Active Directory?
Traditional Active Directory is on-premises and uses domain controllers, while AAD is cloud-native, uses modern authentication protocols (OAuth, SAML), and supports hybrid environments, SSO, and mobile device management.
What are the main AAD licensing tiers?
The main tiers are Free, Office 365 apps, Premium P1, and Premium P2. Free offers basic features, while P1 and P2 add Conditional Access, Identity Protection, and Privileged Identity Management.
Can AAD integrate with on-premises Active Directory?
Yes, via Azure AD Connect, which synchronizes user identities, passwords, and groups from on-prem AD to AAD, enabling hybrid identity management.
Is passwordless authentication supported in AAD?
Yes, AAD supports passwordless authentication using methods like Microsoft Authenticator, FIDO2 security keys, Windows Hello, and SMS/email one-time codes.
In conclusion, Azure Active Directory (AAD) is a cornerstone of modern identity and access management. From secure authentication and conditional access to hybrid integration and advanced threat protection, AAD empowers organizations to embrace digital transformation without compromising security. By understanding its features, licensing, and best practices, businesses can build a resilient, scalable, and compliant identity foundation for the future.
Recommended for you 👇
Further Reading: